This blog is written by the The University of Victoria’s CHISEL Group research team who also authored the report this series is based on.
In today’s ever-evolving cybersecurity landscape, the role of threat hunters is becoming increasingly vital. These professionals are the frontline defenders against sophisticated cyber threats. Threat hunters use a combination of advanced technical skills, situational awareness, and proactive mindsets to protect organizations. This blog post dives into the comprehensive findings from the University of Victoria’s research on threat hunters, offering insights into their workflows, the challenges they face, and captures key threat hunter personas.
In collaboration with OpenText, our team at the University of Victoria’s CHISEL Group embarked on a research journey to uncover the intricacies behind the threat hunting role. This project, led by our dedicated researchers, aims to provide a detailed understanding of threat hunters and their tools, workflows, and challenges. Ultimately, we created personas that will assist in the design and development of tools to support threat hunters in their day-to-day work.
This post is the second in OpenText’s “The Rise of the Threat Hunter” blog series. You can learn more about the series and find links to all our posts here.
Our research
Our team at the University of Victoria are experts in software visualization and social technologies. We study how technology can help people explore, understand, and share complex information and knowledge. Together we conducted 20 interviews with threat hunters across various sectors and from all over the world. The data we gathered uncovered key themes and patterns in threat hunters’ experiences, skills, workflows, and challenges which we then analyzed the data using a qualitative coding. We ultimately developed 17 threat hunter dimensions and four personas that we present in this post.
Our findings were documented in a report reviewed by industry experts at OpenText and can be found here.
Understanding threat hunters: Tasks, tools, roles, skills, and challenges
Threat hunters are crucial in the proactive identification and mitigation of security threats before such attacks can cause significant damage. On any given day threat hunters take on a wide range of tasks. Threat hunters jump from reviewing use cases, to triaging alerts, to creating reports, to conducting meetings, handling escalations, developing rules, managing communications this list goes on! Additionally, managers of threat hunting teams provide high-level security advising and support for active incidents, report to executives.
As the list of tasks in the report shows, the role demands a blend of technical and non-technical skills. Not everyone can conduct an advanced threat hunt requiring problem-solving and analytic abilities and turn around and take complex cybersecurity concepts or research findings and present them clearly and concisely to a company leadership. These skills take time to develop, that’s where continuous learning comes in.
Continuous learning and staying updated with the latest cybersecurity news and trends is a critical aspect of being a threat hunter. While it would be great to learn everything through articles and videos alone, there is a social aspect of continuous learning that can’t be understated. Participation in meetings, working with mentors/mentees and attending conferences allow threat hunters to share expertise and stay informed. Obtaining certificates and continued hunting experience can build a threat hunter confidence; however total confidence is rare due to the rapidly evolving nature of threats.
As with threat hunter skills, there are both technical and non-technical tools are crucial for detecting and mitigating threats, ensuring robust security measures are in place. To highlight just how assorted the toolkits threat hunters use are, we and created a visualization of the tools threat hunters reported using during our interviews, see below.

Every one of these tools address challenges that threat hunters or threat hunting teams face but not every tool is perfect. Some challenges that remain include geographically disperse teams who may fight global time zones, the daily struggle with information overload and fatigue, and a lack of formal handoff protocols. Threat hunters are dynamic individuals that face many challenges that can be solved by developing tools with an underlying understanding of threat hunter needs considered and implemented from day one.
Personas
We want to share everything we learned from our research back with the cyber security community not just because we understand the value of continuing education, but we truly want to see threat hunters succeed. Along with our full report, we have compiled four personas to summarize the key characteristics of threat hunters into a useful device that security managers, product developers, leadership teams, and more can leverage.
During our research we identified 17 key characteristics of threat hunters which we translated into 17 dimensions. You can find the definitions of all 17 dimensions defined on page 17 of the report.
Here are some of the more interesting and impactful dimensions we discovered:
Hunting style (proactive to reactive): This dimension captures a threat hunter’s approach to identifying threats. A proactive style is crucial for anticipating and mitigating potential threats before they cause damage.
Cognitive approach (intuitive/creative to analytical/methodological): This dimension measures how threat hunters process information and solve problems. A balanced approach combining intuition and analytical skills is essential for effective threat hunting.
Learning strategies (self-taught, trial and error, formal certification, mentorship and collaboration): Continuous learning is fundamental, with threat hunters enhancing their skills through various strategies. Effective learning strategies ensure they stay updated with the latest cybersecurity trends.
Tooling landscape (commercial to built in-house): This dimension refers to the types of tools threat hunters use. The ability to leverage both commercial and in-house tools enhances their capacity to detect and respond to threats.
Process initiation (hands-on to tool-led): This dimension captures how threat hunters begin their investigations. Hands-on hunters rely on manual techniques and personal expertise, while tool-led hunters use automated tools and software. Understanding this helps organizations balance manual and automated approaches for optimal threat detection.
Validation of findings (peer to peer to use of resources): This dimension reflects how threat hunters verify their discoveries. Some rely on peer reviews and team discussions, while others use established resources and databases. Recognizing this dimension helps ensure thorough and accurate threat validation processes.
Using these dimensions, we constructed four personas inspired by the threat hunters that we interviewed. We present Olivia, Jay, Thomas, and Ren examples of threat hunter personas.

Olivia is the creative team lead who hunts proactively and excels in leadership, guiding her team, and curating toolkits.
Jay represents the analytical and automation-savvy newcomer, who approaches threat hunting with a problem-solving mindset and strong academic foundations.
Thomas is the experienced, self-taught threat hunter, often referred to as the “Cyberspace Cowboy,” who uses intuition and vast experience to identify threats in smaller teams.
Finally, Ren embodies the managerial role, overseeing the threat hunting team, ensuring effective communication and collaboration, and liaising with clients and organizational leadership.
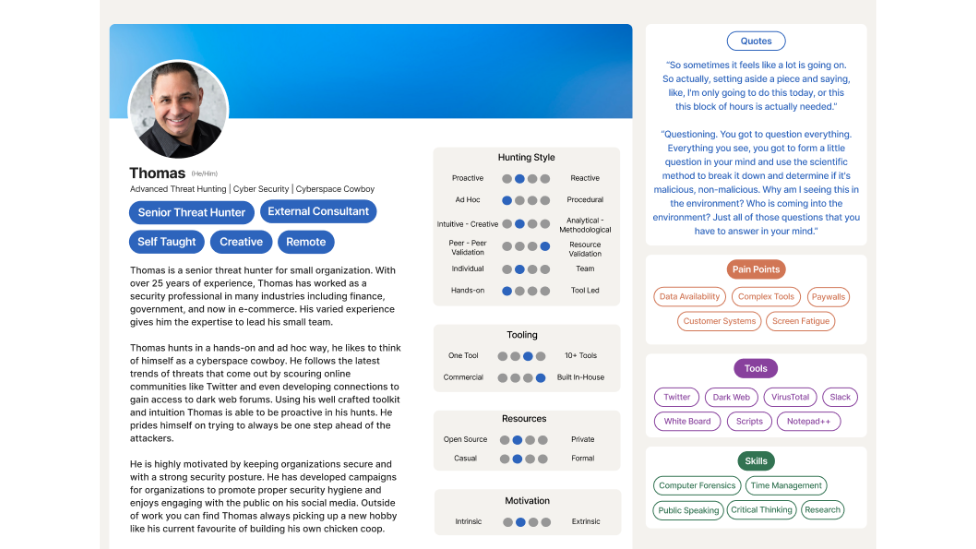
We provide Thomas’ profile as an example and to show how we created a LinkedIn style profile that highlights the key dimensions, skills, and challenges of the threat hunting persona.
Each persona highlights the diverse skill sets and approaches within the threat hunting community, emphasizing the need for both technical acumen and strong interpersonal abilities. These personas can be used as a way of communicating the important needs of threat hunters to the communities and organizations that support them. Personas bring the role of threat hunter to life. Specifically, these personas can be used to incorporate the dynamic and rich characteristics and needs of threat hunters into the design of better tools. We will explore the use of these personas in a future blog post.
Conclusion
Threat hunters play an essential role in cybersecurity. They use a blend of deep technical expertise, continuous learning, and proactive mindsets to safeguard organizations. As we continue to explore the world of threat hunting, our next post will focus on the three key aspects of being a threat hunter, offering deeper insights into the skills and strategies that define this critical profession.
Join us next week as we hear from a veteran threat hunter turned Global Head of Threat Intelligence on the “3 Key Aspects of Being a Threat Hunter.”
The University of Victoria’s CHISEL Group research team
Our team members currently include Samantha Hill (Master’s Student) and Alessandra Milani (PhD student), Arty Starr (PhD student), Norman Anderson (Undergraduate student), David Moreno-Lumbreras (Post Doc), and Margaret-Anne Storey (Professor and Canada Research Chair). Important contributions to this project were previously made by Callum Curtis (Undergraduate student), Marcus Dunn (Former Undergraduate Student), and Enrique Larios Vargas (Researcher at Adyen, previously with UVic). Learn more about the University of Victoria’s CHISEL Group.
Learn more about OpenText Cyber Security
Ready to enable your threat hunting team with products, services, and training to protect your most valuable and sensitive information? Check out our Cyber Security portfolio for a modern portfolio of complementary security solutions that offer threat hunters and security analysts 360-degree visibility across endpoints and network traffic to proactively identify, triage, and investigate anomalous and malicious behavior.



